Featured
Rc4 Stream Cipher Example
Rc4 Stream Cipher Example. They also discuss the stream cipher rc4 in detail, using it as an example for discussing a number of di erent attacks. Some applications using the stream cipher rc4 are attackable because of weaknesses in rc4.
Rc4 is a stream cipher that was created by ron rivest for the network security company rsa security back in 1987. Ztypically, block ciphers may be modified to run in a “stream mode” zwe will examine two of ciphers: A detailed explanation of the rc4 cipher.
January 11, 2021 By Nitesh Malviya.
Of the output remain unused. If you've ever used an application like tsl (transport layer security) or ssl. The example in this section, rc4, can be implemented in just a few lines of code.
The Rc4 Encryption Algorithm, Developed By Ronald Rivest Of Rsa, Is A Shared Key Stream Cipher Algorithm Requiring A Secure Exchange Of A Shared Key.
Public class rc4 { private final byte [] s = new byte [256]; Thus, using stream ciphers the sender and the recipient of the data use the same key to encrypt and decrypt the data. If you've ever used an application like tsl (transport layer security) or ssl.
It's Simple To Apply, And It Works Quickly, Even On Very Large Pieces Of Data.
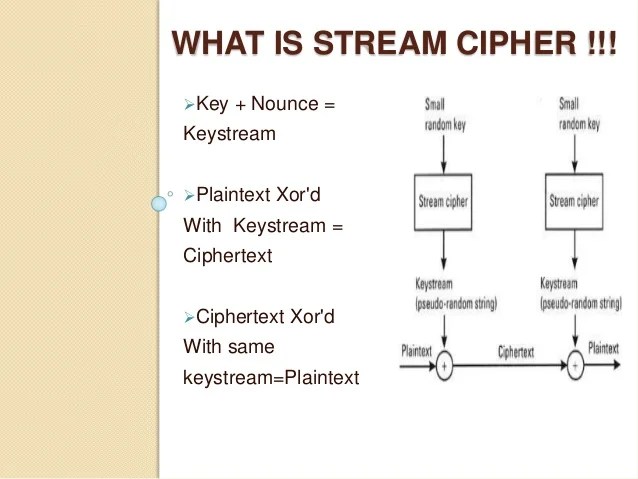
The symmetric key algorithm is used identically for encryption and decryption such that the data stream is simply xored with the generated key sequence. Since then, rc4 has been widely studied and became part of commonly used encryption protocols. A stream cipher is a symmetric key cipher where plaintext digits are combined with a.
Plenty Of Stream Ciphers Exist, But Rc4 Is Among The Most Popular.
While remarkable for its simplicity and speed, multiple vulnerabilities have rendered it insecure. Rc4 (also known as rivest cipher 4) is a form of stream cipher. Private final byte [] t = new byte [256];
It Encrypts Messages One Byte At A Time Via An Algorithm.
Stream ciphers are a very important class of encryption algorithms. Eight to sixteen machine operations are. For example, when the same starting state (seed) is used twice.
Comments
Post a Comment